A recently discovered vulnerability in macOS High Sierra makes it possible for anyone with access to your laptop to quickly create a root account without entering a password, without going through the security protocols you have configured.
It's easy to overstate security concerns. This is not one of those moments. This is really bad.
Puede ingresar a él a través de Preferencias del sistema> Usuarios y grupos> Haga clic en el candado para realizar cambios. Posteriormente use “root” sin contraseña. Y pruébalo varias veces. ¡El resultado es increíble! pic.twitter.com/m11qrEvECs
– Lemi Orhan Ergin (@lemiorhan) 28 November 2017
How the exploit works
Warning: Don't do this on your Mac! We show you these steps to point out how simple this exploit is, but following them will leave your computer insecure. Do. No. Do. This.
The exploit can be executed in many ways, but the easiest way to see how it works is in the System Preferences. The attacker only needs to target Users and groups, click the padlock at the bottom left, and then try to sign in as “root” no password.
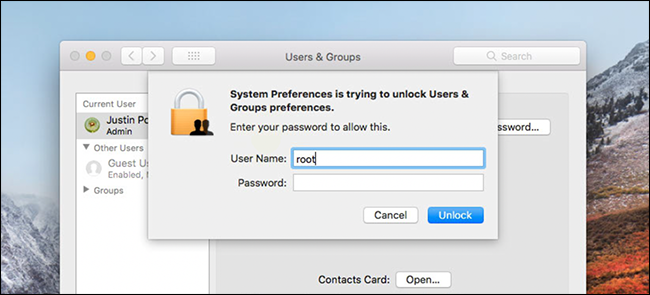

The first time you do this, surprisingly, a root account is created without password. The second time, will log in as root. In our tests, this works regardless of whether the current user is an admin or not.
This gives the attacker access to all administrator preferences in System Preferences … But that's just the beginning, because you have created a new system-wide root user with no password.
After following the steps above, the attacker can log off and select the “Other” that appears on the sign-in screen.


From there, the attacker can enter “root” as a username and leave the password field blank. After hitting Enter, log in with all system administrator privileges.


Now they can access any file on the drive, even if it is protected by FileVault. They can change the password of any user, which enables them to log in and access things like email and browser passwords.
This is the full access. Everything you can imagine an attacker can do, you can do it with this exploit.
And depending on the sharing features you have enabled, it is possible for this to happen remotely. At least one user triggered the exploit remotely using Screen Sharing, as an example.
Si ciertos servicios para compartir están habilitados en el objetivo, este ataque parece funcionar 💯 remoto 🙈💀☠️ (el intento de inicio de sesión habilita / crea la cuenta raíz con pw en blanco) Oh Apple 🍎😷🤒🤕 pic.twitter.com/lbhzWZLk4v
– patrick wardle (@patrickwardle) 28 November 2017
If you have screen sharing enabled, it's probably a good idea to disable it, but who can say how many other possible ways there are to trigger this problem? Twitter users have shown ways to start this using Terminal, which means that SSH is also a potential vector. There are probably endless ways this can be activated, unless you set up a root account yourself and lock it.
How does all this really work? Mac Security Researcher Patrick Wardle explain everything here in great detail. It's quite grim.
Updating your Mac may or may not fix the problem
Al 29 November 2017, there is a patch available for this issue.

But Apple even screwed up the patch. If i was running 10.13, installed the patch and then upgraded to 10.13.1, the problem was reintroduced. Apple should have patched 10.13.1, an update that came out a few weeks earlier, at the same time of launching the general patch. They did not, which means that some users are installing “updates” that revert the security patch, recovering the exploit.
Then, although we still suggest updating your Mac, you should probably also follow the steps below to close the error yourself.
At the same time, some users report that the patch breaks local file sharing. According to Apple, you can fix the problem by opening Terminal and running the following command:
sudo /usr/libexec/configureLocalKDC
File sharing should work after this. This is frustating, but bugs like this are the price to pay for quick patches.
Protect yourself by enabling Root with a password
Even if a patch has been released, some users may still experience the error. Despite this, there is a manual solution that will fix it: you just need to enable the root account with a password.
To do this, head to System Preferences> Users and Groups, then click the item “Login options” in the left panel. Subsequently, Click the button “Join” next to “Network Account Server” and a new panel appears.
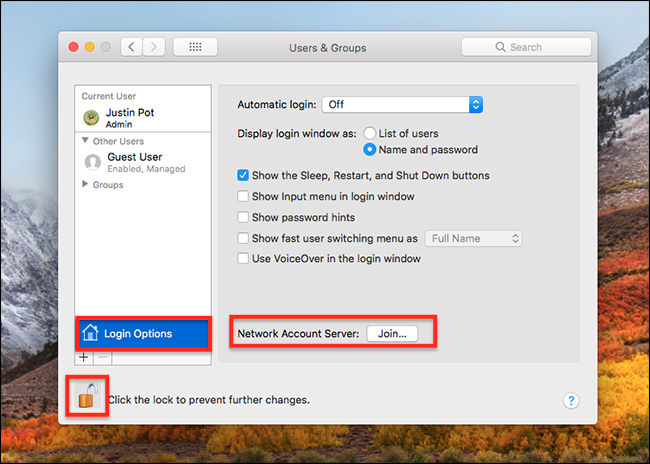

Click on “Open Directory Utility” and a new window will open.


Click the lock button, then enter your username and password when prompted.
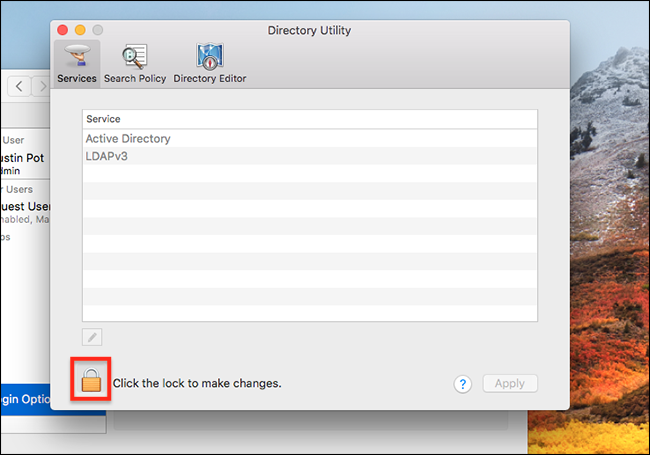

Now click Edit> Enable Root User on the menu bar.


Enter a strong password.
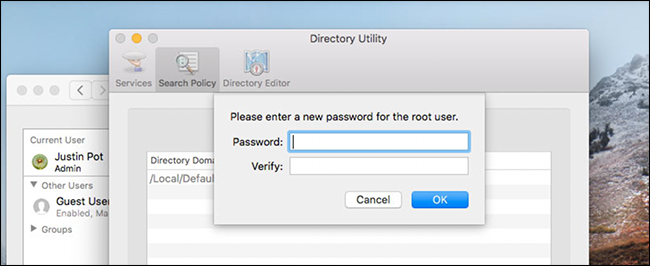

The exploit will no longer work, because your system will already have a root account enabled with a real password attached.
Keep installing updates
Let's make this clear: this was a big mistake on Apple's part, and the security patch that doesn't work (and break file sharing) it's even more embarrassing. Having said that, the exploit was bad enough that Apple had to move quickly. We think you should absolutely install the patch available for this issue and enable a root password. Hopefully, Apple will fix these issues with another patch soon.
Update your Mac: do not ignore those indications. They are there for a reason.