Get serious about cybersecurity and use SSH keys to enter remote logins. They are a more secure way to connect than passwords. We show you how to generate, install and use SSH keys on Linux.
What's wrong with passwords?
Secure Shell (SSH) is the encrypted protocol used to log into user accounts on remote Linux or Unix-like computers. Regularly, these user accounts are protected by passwords. When you log in to a remote computer, you must provide the username and password of the account you are logging into.
Passwords are the most common means of ensuring access to computing resources. Nonetheless, password-based security has its flaws. People choose weak passwords, share passwords, use the same password on multiple systems, etc.
SSH keys are much more secure and, once configured, they are as easy to use as passwords.
What Makes SSH Keys Secure?
SSH keys are created and used in pairs. The two keys are linked and cryptographically secure. One is your public key and the other is your private key. They are linked to your user account. If multiple users on a single computer use SSH keys, each will receive their own key pair.
Your private key is installed in your home folder (generally) and the public key is installed on the remote computer (or computers) which you will need to enter.
Your private key must be kept safe. If others can enter it, you are in the same position as if your password had been discovered. A sensible precaution, and highly recommended, is that your private key is encrypted on your computer with a robust passphrase.
The public key can be freely shared without compromising its security. It is not feasible to determine what the private key is from an examination of the public key. The private key can encrypt messages that only the private key can decrypt.
When you make a connection request, the remote computer uses your copy of your public key to create an encrypted message. The message contains a session ID and other metadata. Only the computer in possession of the private key, his computer, can decrypt this message.
Your computer accesses your private key and decrypts the message. It then sends its own encrypted message to the remote computer. Among other things, this encrypted message contains the session ID that was received from the remote computer.
The remote computer now knows that you must be who you say you are because only your private key could extract the session ID from the message it sent to your computer.
Make sure you can enter the remote computer
Make sure you can connect and log in remotely to the remote computer. This proves that your username and password have a valid account configured on the remote computer and that your credentials are correct..
Do not try to do anything with SSH keys until you have verified that you can use SSH with passwords to connect to the target computer.
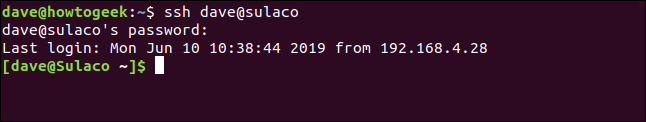
In this example, a person with a user account called dave is connected to a computer called systempeaker . They will connect to another computer called Sulaco.
They enter the following command:
ssh dave@sulaco


They are asked for their password, they enter it and connect to Sulaco. Your command line prompt changes to confirm this.

That's all the confirmation we need. Then user dave can disconnect from Sulaco with the exit command:
exit


They get the disconnect message and their command line goes back to dave@systempeaker.
RELATED: How to connect to an SSH server from Windows, MacOS or Linux
Create an SSH key pair
These instructions were tested on Ubuntu Linux distributions, Fedora and Manjaro. In all cases, the procedure was identical and there was no need to install any new software on any of the test machines.
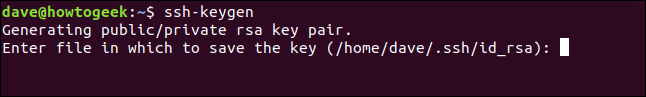
To generate your SSH keys, type the following command:
ssh-keygen


The generation procedure begins. You will be asked where you want your SSH keys to be stored. Press the Enter key to accept the default location. The folder permissions will protect it for your use only.

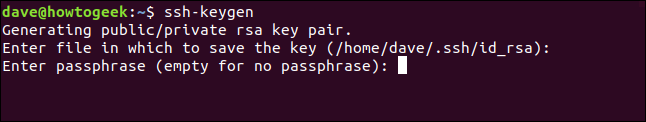
You will now be prompted for a passphrase. We strongly suggest that you enter a passphrase here. And remember what it is! You can press Enter to not have a password, but this is not a good idea. A passphrase made up of three or four disjointed words, linked together, will form a very strong passphrase.

You will be asked to enter the same password one more time to verify that you have typed what you thought you typed.
SSH keys are generated and stored for you.
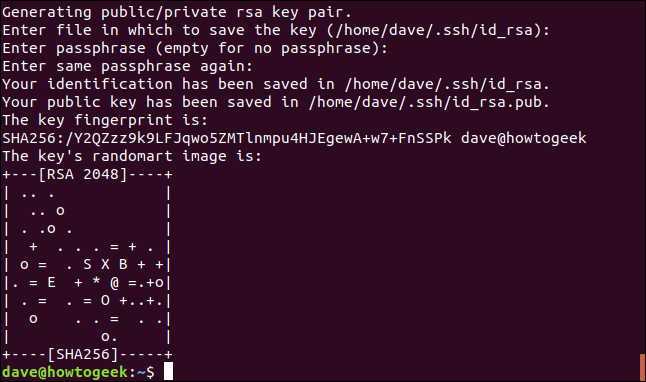

Puede ignorar el “randomart” que se muestra. Some remote computers may show you their random art every time you connect. The idea is that it recognizes if the random art changes and suspects the connection because it means that the SSH keys for that server have been altered.
Installing the public key
We need to install your public key in Sulaco , the remote computer, so you know that the public key belongs to you.
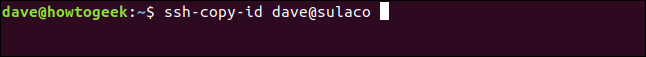
We do this using the ssh-copy-id command. This command establishes a connection to the remote computer as normal. ssh command, but instead of allowing you to login, transfer the public SSH key.
ssh-copy-id dave@sulaco

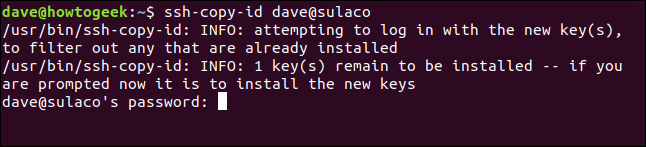
Even when you are not logging into the remote computer, you still need to authenticate with a password. The remote computer must identify which user account the new SSH key belongs to.
Please note that the password you need to provide here is the password of the user account you are logging into. This is no the passphrase you just created.

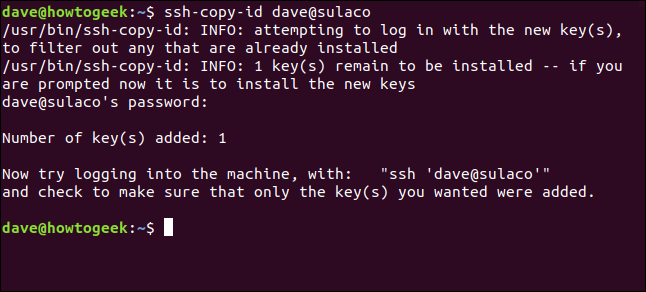
When the password has been verified, ssh-copy-id transfers your public key to the remote computer.
You will return to your computer's command prompt. It is not connected to the remote computer.

Connection via SSH keys
Let's follow the suggestion and try to connect to the remote computer.
ssh dave@sulaco


Because the connection procedure will require access to your private key, and because you protected your SSH keys behind a passphrase, you will need to provide your passphrase for the connection to continue.
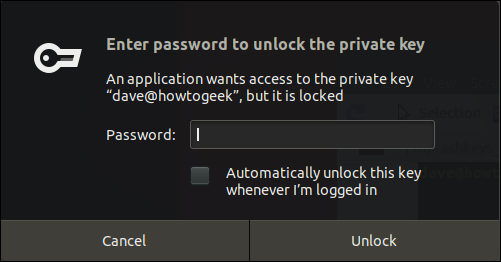

Enter your password and click the Unlock button.
Once you have entered your passphrase in a terminal session, you won't have to enter it again as long as you have that terminal window open. You can connect and disconnect from as many remote sessions as you want, without re-entering your password.
Puede marcar la casilla de verificación de la opción “Desbloquear automáticamente esta clave cada vez que inicie sesión”, but it will reduce your security. If you leave your computer unattended, anyone can make connections to remote computers that have their public key.
Once you enter your password, will be connected to the remote computer.
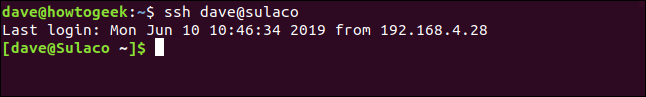

To verify the procedure one more time from one end to the other, disconnect with exit command and reconnect to the remote computer from the same terminal window.
ssh dave@sulaco
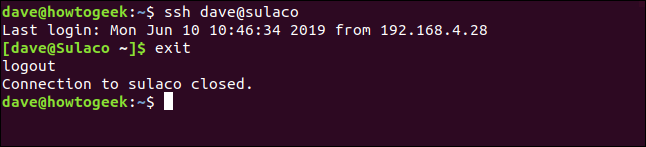

You will be connected to the remote computer without requiring a password or passphrase.
No passwords, but improved security
Cybersecurity experts talk about something called security friction. That's the least pain you have to endure to get the added security gain. In general, some extra steps are required to adopt a safer working method. And most people don't like it. Actually, prefer less safety and lack of friction. That is human nature.
With SSH keys, you get more safety and comfort. It is definitely a mutual benefit.
setTimeout(function(){
!function(f,b,e,v,n,t,s)
{if(f.fbq)return;n=f.fbq=function(){n.callMethod?
n.callMethod.apply(n,arguments):n.queue.push(arguments)};
if(!f._fbq)f._fbq = n;n.push=n;n.loaded=!0;n.version=’2.0′;
n.queue=[];t=b.createElement(e);t.async=!0;
t.src=v;s=b.getElementsByTagName(e)[0];
s.parentNode.insertBefore(t,s) } (window, document,’script’,
‘https://connect.facebook.net/en_US/fbevents.js’);
fbq(‘init’, ‘335401813750447’);
fbq(‘track’, ‘PageView’);
},3000);