Do you want to encrypt important files, but not the entire hard drive of your Linux system? If so, we suggest gocryptfs. You will get a directory that, essentially, encrypt and decrypt everything it stores.
gocryptfs offers protection against data breaches
Privacy is great news. Hardly a week goes by without a breach being announced in one organization or another. Companies report recent incidents or disclose violations that occurred long ago. In both cases, it's bad news for those whose data has been exposed.
Because millions of people use services like Dropbox, Google Drive, and Microsoft OneDrive, a seemingly endless stream of data is sent to the cloud every day. If you store some (the all) your data in the cloud, What can you do to protect classified information and private documents in the event of a breach??
Data breaches come in all shapes and sizes, decidedly, and they are not limited to the cloud. A removable memory stick or stolen laptop is just a minor data breach. But scale is not the critical factor. If the data is sensitive or confidential, someone else having them could be disastrous.
One solution is to encrypt your documents. Traditionally, this is done by encrypting your hard drive in its entirety. This is safe, but it also slightly slows down your computer. At the same time, if you suffer a catastrophic failure, can complicate the procedure of restoring your system from backups.
the gocryptfs system enables you to encrypt only the directories that need protection and avoid encryption and decryption overhead throughout the entire system. It's fast, lightweight and easy to use. It is also easy to move encrypted directories to other computers.. As long as you have the password to access that data, will not leave a trace of your files on the other computer.
the gocryptfs The system is built as a lightweight, encrypted filesystem. It can also be mounted with regular non-root accounts because it uses the File system in user space (FUSIBLE) package. This acts as a bridge between gocryptfs and the kernel filesystem routines you need to have access to.
Gocryptfs installation
Install gocryptfs en free, write this command:
sudo apt-get install gocryptfs
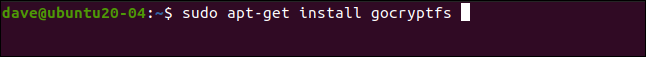

To install it in Fedora type:
sudo dnf install gocryptfs
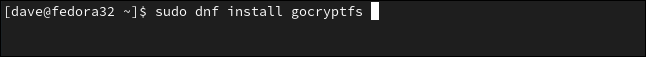

In Manjaro, the command is:
sudo pacman -Syu gocryptfs

Creating an encrypted directory
Part of the glory of gocryptfs is how simple it is to use. The principles are:
- Create a directory that contains the files and subdirectories you are protecting.
- Use
gocryptrfsto initialize that directory. - Create an empty directory as mount point and then mount the encrypted directory on it.
- At the mount point, you can view and use the decrypted files and create new ones.
- Unmount the encrypted folder when done.
Let's create a directory called “vault” to contain the encrypted data. To do it, we write the following:
mkdir vault


We need to initialize our new directory. This step creates the gocryptfs file system within directory:
gocryptfs -init vault
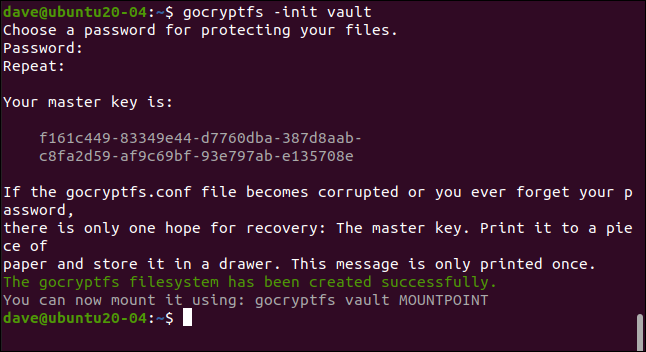

Enter a password when prompted; you will type it twice to make sure it is correct. Choose a strong one: three unassociated words that include punctuation, digits or symbols is a good template.
Your master key is generated and displayed. Copy and keep it in a safe and private place. In our example, we are creating a gocryptfs directory on a research machine that gets deleted after each post is written.
As needed for an example, you can see the master key for this directory. You will definitely want to be much more reserved with yours. If someone gets your master key, you can have access to all your encrypted data.
If you change to the new directory, you will see that two files have been created. Write the following:
cd vault
ls -ahl
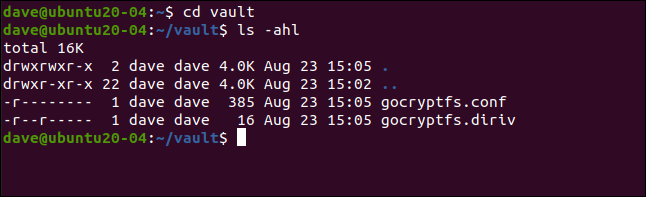

“Gocryptfs.diriv” is a short binary file, while “gocryptfs.conf” contains settings and information that you should keep safe.
If you upload your encrypted data to the cloud or back it up to a small, transportable medium, do not include this file. Despite this, if you back up to a local media that remains under your control, you can include this file.
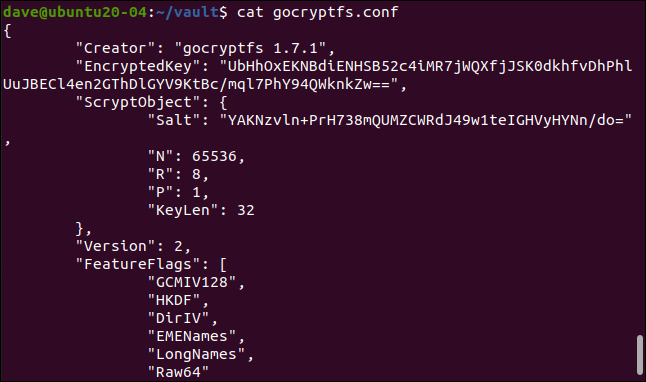
With enough time and effort, it might be feasible to extract your password from the entries of “encrypted key” and “Salt”, as it's shown in the following:
cat gocryptfs.conf

Mounting the encrypted directory
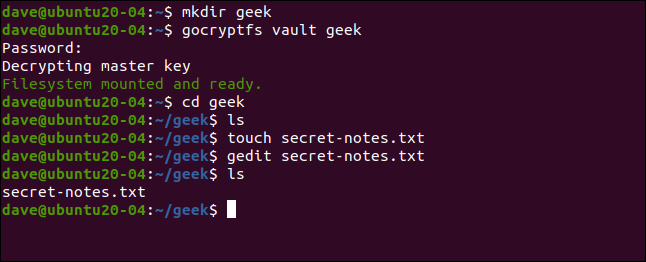
The encrypted directory is mounted on a mount point, which is just an empty directory. Let's create one called “geek”:
mkdir geek
Now we can mount the encrypted directory on the mount point. Strictly speaking, what is really mounted is the gocryptfs file system within the encrypted directory. We are asked for the password:
gocryptfs vault geek
When the encrypted directory is mounted, we can use the mount point directory in the same way as we would any other. Everything we edit and create in this directory is written to the mounted encrypted directory.
We can create a simple text file, like the following:
touch secret-notes.txt
We can edit it, add content to it and then save the file:
gedit secret-notes.txt
Our new file has been created:
ls

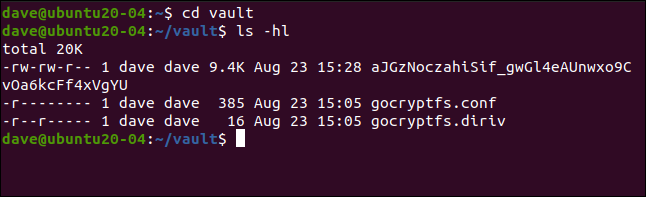
If we change to our encrypted directory, as it's shown in the following, we see that a new file has been created with an encrypted name. You can't even tell what type of file it is by the name:
cd vault
ls -hl

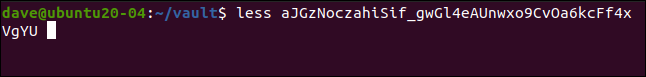
If we try to see the content of the encrypted file, we can see that it is truly coded:
less aJGzNoczahiSif_gwGl4eAUnwxo9CvOa6kcFf4xVgYU

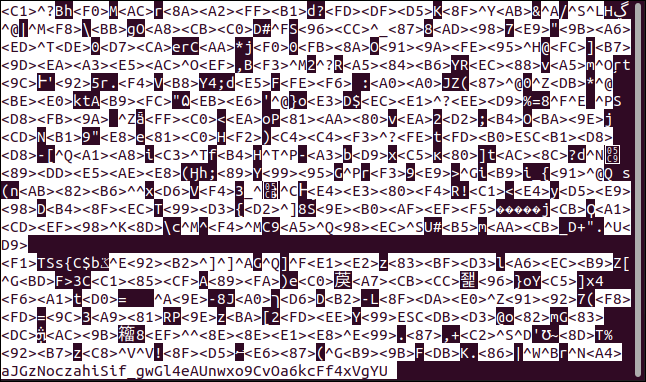
Our simple text file, shown below, is now anything but easy to decipher.

Unmounting the encrypted directory
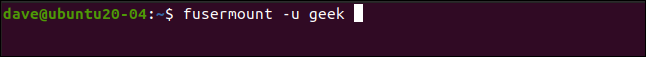
When you are done with your encrypted directory, you can disassemble it with the fusermount command. As part of the FUSE package, the following command unmounts the gocryptfs file system within directory encrypted from mount point:
fusermount -u geek

If you type the following to verify your mount point directory, you will see that it is still empty:
ls


Everything you did is safely stored in the encrypted directory.
Simple and safe
Simple systems have the advantage of being used more frequently, while more complicated processes tend to stay on track. Using gocryptfs not only is it simple, it is also safe. Simplicity without security wouldn't be worth it.
You can create as many encrypted directories as you need or just one to store all your confidential data. Also you may want to create some aliases to mount and unmount your encrypted file system and further simplify the procedure.
RELATED: How to create aliases and shell functions in Linux