Every minute of production downtime will generally cost the company money. If your application has a serious obstacle causing the battery to break, is on a trip. Learn what battery shredding is in advance and what can be done about it!!
What is it Stack Smashing?
Working as a quality assurance engineer, sooner or later one will come across the term pile crush. As a developer, this term is likely to be discovered even earlier, especially if an error has been entered in the code, what causes a broken battery. It's relatively easy (like in 'something easy’) for a developer to make a mistake that introduces battery break. As a user, when I learn to break batteries, the damage is likely already done.
Battery breakage can occur unintentionally, as an example, when the developer introduced a bug that caused the stack to crash, or maliciously, an attacker who somehow tries to overflow or corrupt a program's stack.
Stack smashing is a definition with a somewhat vague definition that can point to various problems and can come from a range of sources. The two most important problems that can cause the battery to break are; 1) to write / over-allocating too much data in a given part of the stack, thus overwriting another part of the stack, and 2) where some external source (malicious or not) overwritten the stack of another program, even though this is much less common .
Then, What is a stack? This is also a loosely defined definition. In general terms, a stack refers to a program processing stack, a stack of functions defined in a program / given software code.
Start by imagining a stack of stacked bathroom tiles, ready to be used by a tiler. This is a pretty good representation of a stack of computers., with some modifications. If each mosaic were a little displaced from the previous one, it would be a better image, and soon we will see why.


Imagine that each stacked tile is a function in the computer program. The most basic function is at the bottom and could be, as an example, the main() function in a C or C program ++. C y C ++ they are two programming languages that use the stack extensively.
Each of these functions in program C / C ++ it will have a name and probably a set of incoming and outgoing variables. In simplified terms, imagine if one of those variables had a length of 10 characters and some other function accidentally typed 100 characters in that variable. This can damage the entire stack..
In terms of the tile example above, imagine someone with a hammer hitting the first tile too hard and thus breaking all the other tiles. there you go; pile breaking 😉
The analogy works because, just as all the tiles are now broken in our fictitious memory image, a broken battery will result in 'Broken functions’ If you pretend. Each tile offset is a more deeply nested function; more on broken functions in the next section.
Depuration Battery (s) shattered
Whereas technically a reference to 'Broken functions’ may not be totally correct, In other words, there is probably only one broken function, and even there may not be a broken function when there is an external attack or a malfunctioning program, it's a great way to think about a broken battery.
Suddenly, variable and function names can be altered, there is a backtrace (the flow of functions that the computer took to arrive at a given function that crashed, and (in our example) broke the stack) it no longer makes sense.
In general terms, when we look at a backtrace, will have a clear flow of functions that were called. Although a failing program cannot immediately be called 'healthy', in terms of recoil / depuration, this is what a 'healthy' throwback looks like:
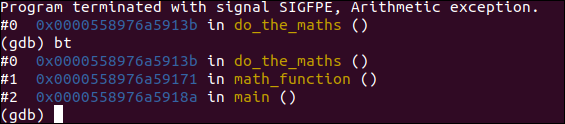

Despite this, when a battery is bad, debugging becomes much more difficult. The stack can look like this:
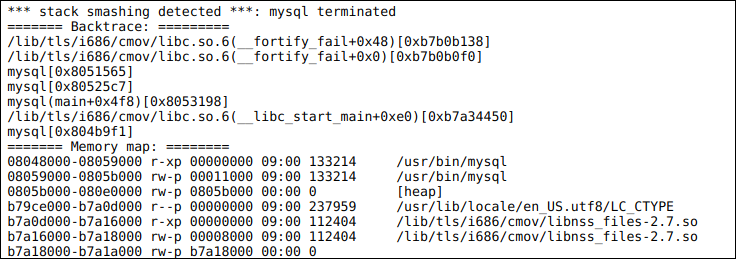

This is an example of a stack break problem that happened in MySQL, the database server (Ask the log.txt attached to Error de MySQL 37815 for full output) on 2008, which caused the database server daemon (mysqld) to end.
While the operating system library libc.so.6, in this circumstance, seems to have handled the breaking stack quite well (using some fortification functionality in the __fortify_fail function), the problem existed somewhere in the code and has since been fixed.
Also note that in this circumstance, we don't see function names resolved, we are only shown the binary name (curiously, the problem seems to have been with the client (mysql) causing the server (mysqld) to end) What is it mysql, along with a memory address of the function: mysql[0x8051565], mysql[0x80525c7] and mysql(main+0x4f8)[0x8053198].
Regularly, when we use debug symbols (see below a post on GDB that explains what debug symbols are in detail), we would see function names with variables, and even with some levels of optimization / binary minification implemented, at least we would see the function names, like what we see in the first backtrace ‘healthy’ anterior.
Despite this, in the case of a broken battery, the output of function names, variable names or values is never guaranteed and, often, a verbiage is completed 🙂 We can even see different names of functions or a shattered pile (another jargon often used by IT folks) different function names that don't make much sense (and they are probably fictitious / false since the stack was somehow overwritten).
This makes it more difficult for both the test engineer (which can end up with many different results for a single error, which complicates the handling of the known error filtering mechanism) as for the developer (which you will probably have to use a step by step trace or a reverse run debugger like RR to discover the error in question).
What to do when you face Stack Smashing?
If you encounter broken batteries, the first thing to do is to understand the problem and the environment a little better to know the source. If you have a popular web server exposed on the internet with many game users trying to win a tournament while the server is also mining Bitcoin, you'll want to take over a foul play opportunity and find out if someone is messing with the server.
Despite this, In most cases, the problem will be just an application error. While i say ‘solo’, the problem can be very important, may result in downtime of services, it can cost a lot of money and, to end, it can't be fixed. As an example, a database server may persistently fail when started due to data being in a certain state in combination with a deficiency or limitation in code.
If such a situation is aggravated by not breaking the battery, or put another way, not being able to generate a clean follow-up of the problem, debugging will be more complicated and, sometimes, almost impossible. Despite this, do not worry, the same basic debugging as with any bugs or errors / failure / application problem remains the same.
Please read all log files carefully before, during and after the problem occurred. Take some backups and then try the operation again. Does it fail again or not? Investigate the bugs, the parts of the stack and even the frames (In other words, the individual stack functions displayed, As the do_the_maths function in our 'healthy stack trace’ original) can be placed in your favorite search engines.
Concatenar (with a space) the most selective locked frames (superior) and searching for the same online often gives you an existing bug report for the problem you are facing. Even so, in the event of a battery break, these frames are likely (function names) have been spoiled and, because, can no longer be used in the same way. If you see an affirmation message (an assertion instituted by the developer in the code) of any type, look it up also.
Always file a new bug report if the problem still doesn't seem to be logged online (You may be helping others who are seeing the same!) And provide as much information about the problem as you can find. Hundreds of bug reports against so many applications are logged online every day. Hopefully, the support team of your stack destruction application is enabled to help you quickly.
You may also like to read our post Debugging with GDB: Introduction below, since it is based on how C and C programs can be debugged ++ (and others) with GDB debugger. It also explains in more detail the concepts of a stack.