In software development, It seems like no matter where I go, no matter who i talk to, containers are the new normal. If you are not yet developing or migrating your application, you are creating support systems that use them to support a legacy application. Containers are everywhere.
Despite this, this means that, as an engineer, you will need to put your containers somewhere. In the old times, this meant building an artifact of some kind, either a binary or a file, later write it to a disk or a shared file and distribute it. In the container ecosystem, it will be a container registry and the artifacts you create will be container images.
Ideally, a container registry would be in a safe place that could automate some of the work for you, like scanning containers and triggering actions on every commit or on a schedule. Fortunately, Azure has you covered with all of the above with Azure Container Registry, the ACR for short.
Prerequisites
To move on, you will need the following:
- An Azure account
- A container to push and pull the repository
- (Optional) A PowerShell terminal authenticated to Azure or a CloudShell instance
The container does not have to be anything other than hello-world because this is a tutorial on container logs, not the containers themselves. If you are not familiar with Docker or containers, you can get more information about them. here.
Creating the Registry
The first thing to do is create a record, primero con Azure Portal y posteriormente con Azure PowerShell.
Usando el portal
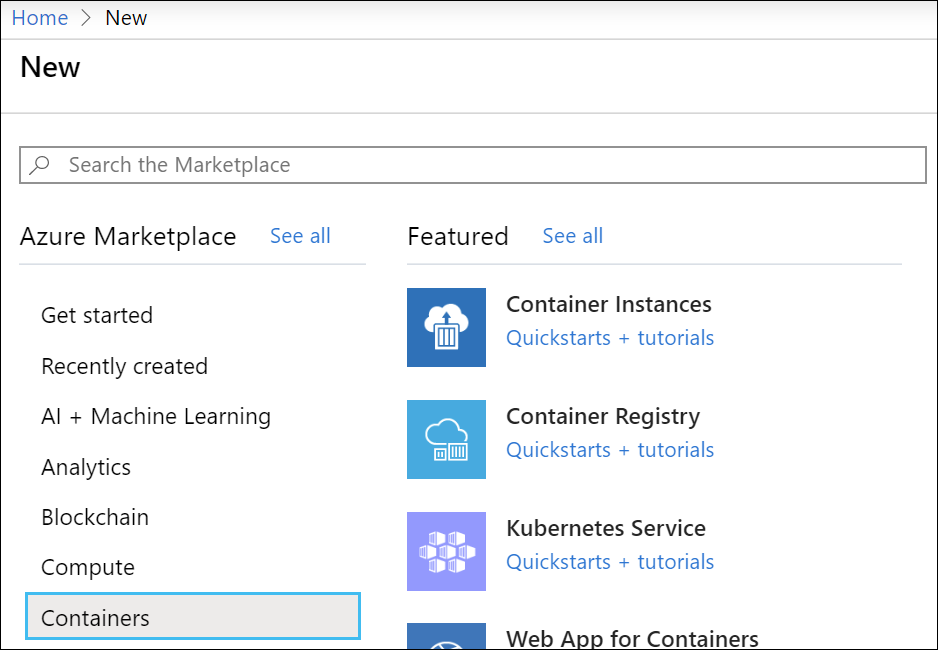
Go to “Crear un recurso”, posteriormente busque en Contenedores> Registro de contenedores.


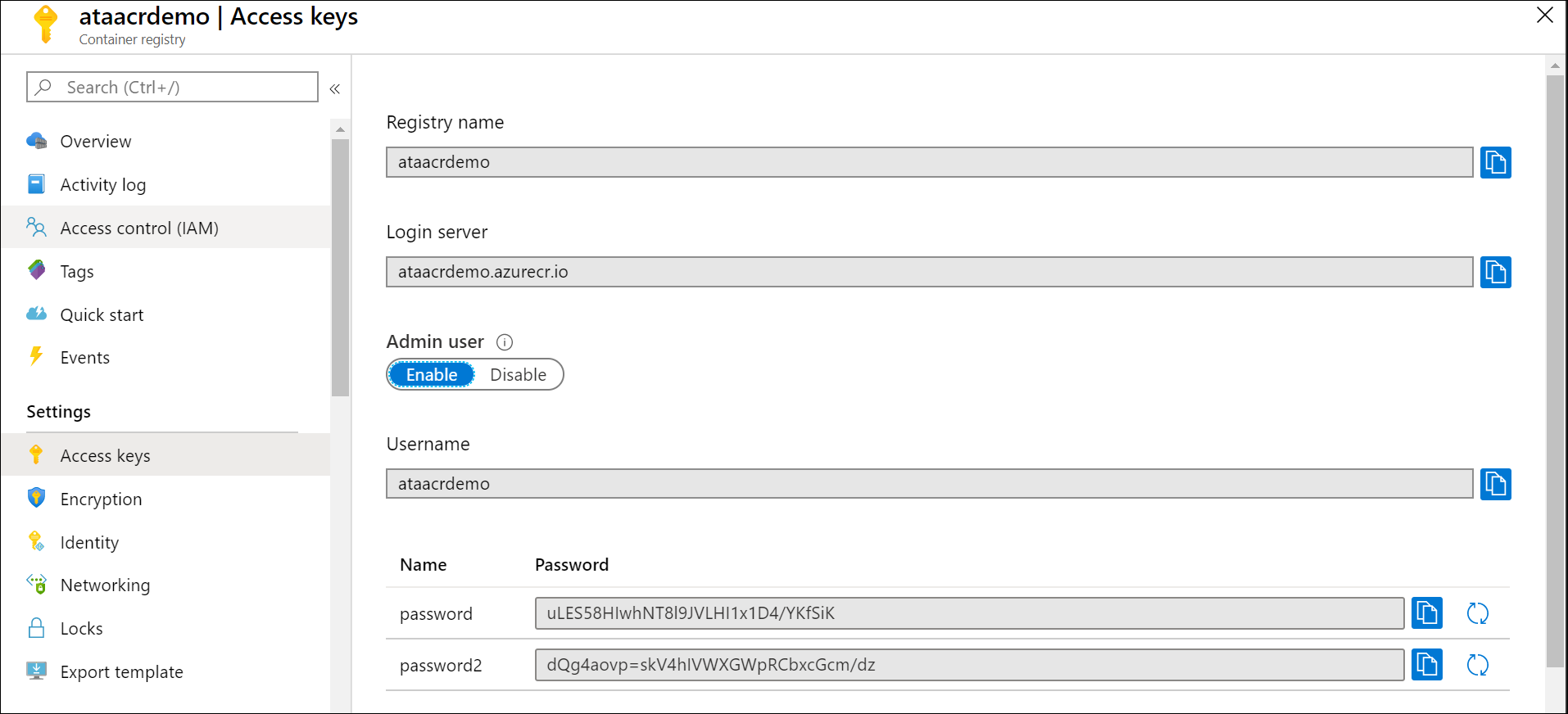
Once it's provisioned, vaya a la página de recursos y busque la pestaña “Access keys”. From here, asegúrese de habilitar la opción “Administator” para que pueda iniciar sesión usando la CLI más adelante.

Utilizar Azure PowerShell
Con Azure PowerShell, this is done with a line, either in a CloudShell instance or in a locally authenticated PowerShell console with the Azure PowerShell module installed.
New-AzContainerRegistry -ResourceGroupName <Resource Group Name> -Name <Registry Name> -EnableAdminUser
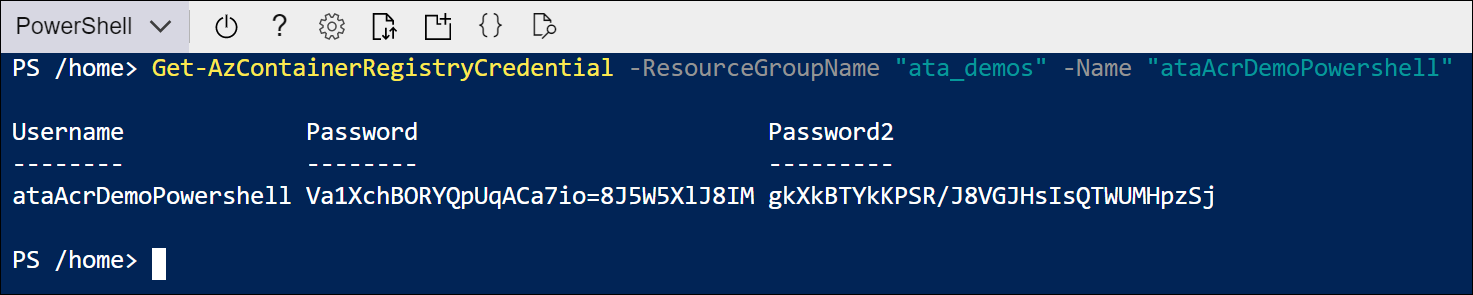
Next, you can use the Get-AzContainerRegistry cmdlet to list the records associated with your tenant. You will still need the LoginServer to submit your image to the registry, but you can extract it from Azure PowerShell shown in the rest of the demo.
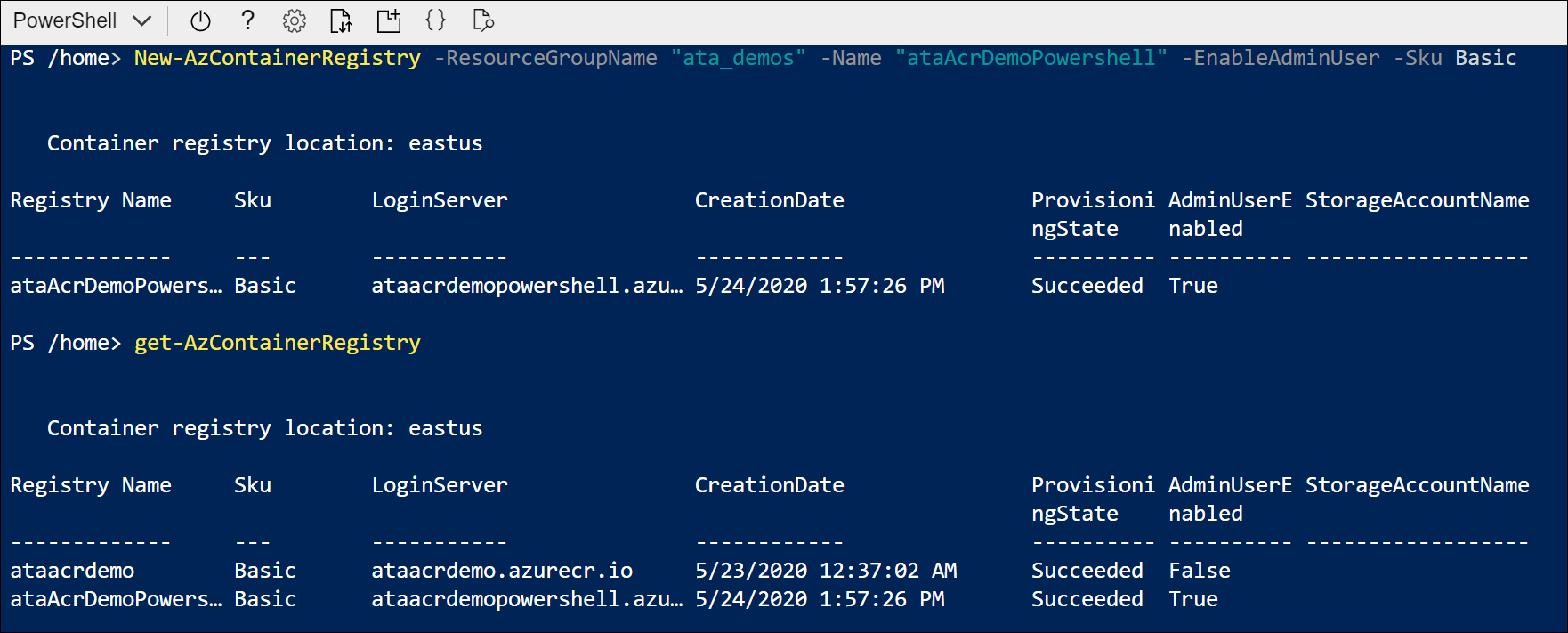

As long as you have included the -EnableAdminUser flag, you can also use the Get-AzContainerRegistryCredential cmdlet to get the login credentials for the next step.

Push the image to ACR
Now that the registry and user are configured, it's time to log in and send you a picture. You can log in using the docker login command. If you are using a script, make sure credentials are not displayed in plain text, passing them this way or using Azure Key Vault.
# Azure PowerShell
$RG_NAME = <Resource_Group_Name>
$ACR_NAME = <Registry_Name>
$registry = Get-AzContainerRegistry -ResourceGroupName $RG_NAME -Name $ACR_NAME
$creds = Get-AzContainerRegistryCredential -Registry $registry
$creds.Password | docker login $registry.LoginServer -u $creds.Username --password-stdin
If you are doing it manually, just run docker login <RegistryURL> and replace “
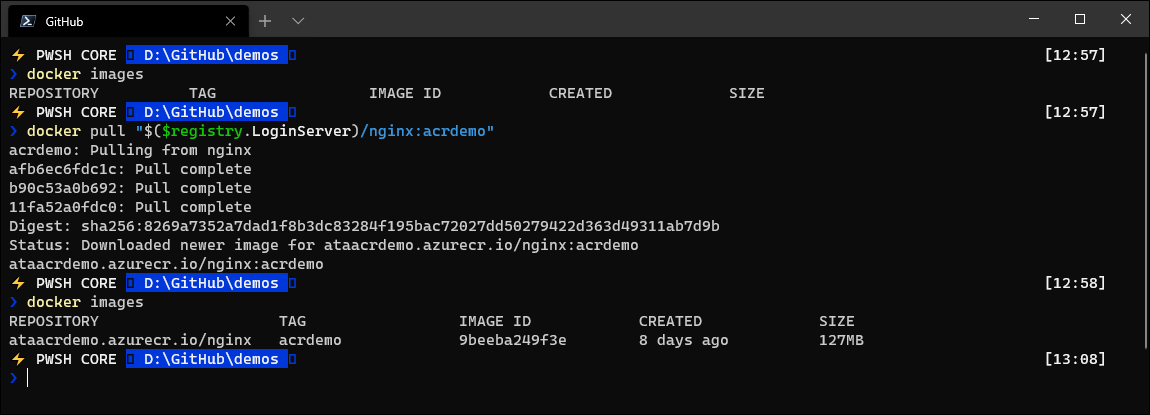
Now that you have logged in, you can send and pull container images from repository as much as you like. Once you have built or checked out a container locally, use el docker tag command to add record url and version tag to image, later the docker push command to push it to ACR. It should look something like this:
# Docker CLI
docker tag <Image_Name> <Registry_URL>/<Image_Name>:<Version_Tag>
docker push <Registry_URL>/<Image_Name>:<Version_Tag>
With the image in ACR, you can use the docker pull from any authenticated device to extract the image and run it.

Summary
At this stage, You should already be familiar with how to set up a record in ACR through the Azure portal or Azure PowerShell, as well as the way to insert and extract containers from it.
From here, you can look to enable container vulnerability scanning with Azure Security Center or automation using ACR Tasks.